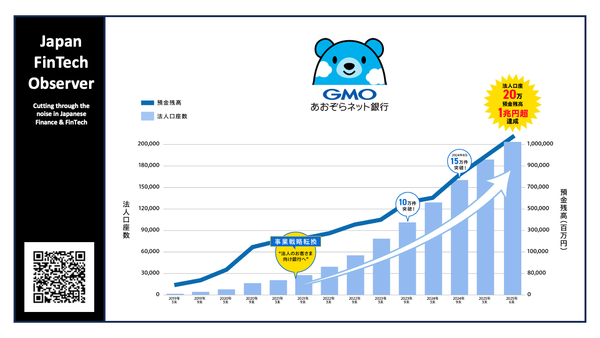
LINE Yahoo’s progress report on the administrative guidance concerning data leaks
LINE Yahoo has submitted its second regular report, outlining the progress made by the company in addressing the administrative guidance…

LINE Yahoo has submitted its second regular report, outlining the progress made by the company in addressing the administrative guidance received from the Ministry of Internal Affairs and Communications (MIC) of Japan. The report primarily focuses on three areas outlined in the April 16 administrative guidance.
Fundamental Review and Enhancement of Security and Outsourcing Management
This section details the progress made in implementing the planned measures to strengthen security and outsourcing management, as promised in the April 1 report.
- Separation of Private Network with NAVER Cloud: The company has taken steps to segregate its private network from NAVER Cloud, a key area of concern highlighted by MIC. This includes strengthening network access control by reviewing and modifying unnecessary communication permissions, verifying incident response readiness, and implementing firewall policies to control outbound traffic from the legacy LINE data center to the NAVER Cloud data center. The company is also progressing towards implementing two-factor authentication for employee systems located in the legacy Yahoo data center.
- Separation from NAVER and NAVER Cloud Systems: To mitigate risks associated with shared systems, the company is actively working on separating its systems from those managed by NAVER and NAVER Cloud. This involves migrating employee-facing systems by March 2025 for the company and domestic subsidiaries, and by March 2026 for overseas subsidiaries. Separation from systems used for technical aspects, system planning, and development is targeted for completion by March 2026. The company is continuously reviewing and updating firewall policies to separate servers used for the legacy LINE services.
- Separation of Authentication Infrastructure: The company has successfully removed unnecessary employee information from the NAVER authentication infrastructure and ceased password synchronization with its own authentication system. The removal of remaining employee information from the NAVER Cloud data center is ongoing and expected to be completed by April 2025 for the company and domestic subsidiaries, and by April 2026 for overseas subsidiaries. The company is committed to stopping the use of authentication infrastructure managed by NAVER and NAVER Cloud for all systems by March 2026.
- Domestication of SOC and Log Acquisition: The company has transitioned its Tier 1 Security Operations Center (SOC) monitoring operations from NAVER Cloud to a domestic company, with full-scale operation starting from October 1, 2024. Furthermore, the company is strengthening its incident response capabilities by defining clear incident response procedures, investigation scope determination processes, and stakeholder roles and responsibilities.
- Review of Security Management Measures: The company has defined and identified critical systems based on the security requirements for each lifecycle stage of its information systems. The next steps involve verifying compliance with security measures for critical systems by October 2024, conducting risk assessments for non-compliant areas by December 2024, and formulating a plan to update security measures based on the latest trends by December 2024.
- Penetration Testing: A penetration test conducted by an external security firm revealed areas for improvement despite highlighting the effectiveness of the implemented security measures. The company has developed a remediation plan based on the findings and will prioritize addressing high-risk issues by March 2025. The company aims to maintain a robust security posture by conducting annual penetration tests.
- Improvement of Behavioral Detection Mechanisms: The company conducted a security assessment to evaluate the effectiveness of its behavioral detection and correlation analysis rules against common attack methods. Remediation efforts are underway to address undetected attack simulations, with completion expected by February 2025. The company is dedicated to continuously improving its detection capabilities through regular rule optimization and threat intelligence integration.
- Review of Outsourcing Management: The company has implemented a new outsourcing management framework based on the “Basic Policy on Outsourcing Management” and “Basic Rules on Outsourcing Management” enforced on July 1, 2024. The new framework includes supplier assessments and project risk assessments.
- Provision of Company PCs to Outsourced Vendors: The company has provided its own or group company PCs with equivalent security measures to vendors accessing its network using company-issued accounts. The company is expanding the scope of PC provision to other vendors accessing its network to enhance security and oversight.
Fundamental Review and Enhancement of Security Governance across the Entire Group, including Parent Companies
This section addresses the progress made in reviewing and enhancing security governance across the entire corporate group, including the parent companies.
- Reducing Dependence on NAVER: The company has outlined its plan to reduce its reliance on NAVER’s systems and services. It has identified specific outsourced operations to be terminated or scaled back by December 2025 for services from NAVER and NAVER Cloud and by March 2026 for those from other NAVER Group companies. Outsourcing related to technology, system utilization, service planning, and development will also be scaled back by March 2026. The company completed its risk assessment for remaining operations by September 2024 and is developing an action plan for identified risks.
- Review of Capital Relationships: While the company requested its parent company, A Holdings, to review the capital relationship with SoftBank and NAVER to address concerns regarding the influence of outsourced companies with significant capital ties, both companies indicated difficulties in making immediate changes. The company will continue to engage in discussions to find a feasible solution.
- Review of Management Structure: The company has strengthened its governance structure by adding four independent outside directors and audit and supervisory board members, bringing the total number of directors to six.
- Enhancing Group-wide Security Governance: A steering committee comprising the CEOs of the company and NAVER is actively discussing the complete separation of outsourced operations. The newly established “Group CISO Board” focuses on standardizing security practices across the group and elevating the overall security level. Meanwhile, the “Security Governance Committee,” also established in April 2024, oversees company-wide security governance, including reviewing progress on corrective measures, promoting security awareness, and enhancing overall security posture.
Thorough User Support:
This section outlines the company’s efforts to ensure adequate user support and address potential secondary damage.
- Proactive Communication and Transparency: The company continuously provides updates on its corrective measures and their progress through a dedicated page on its corporate website launched on April 1, 2024.
- Secondary Damage Mitigation: While no secondary damage has been confirmed as of the report’s publication date, the company is taking proactive measures to identify and address potential incidents. This includes enhanced monitoring of the dark web and other sources to detect potential data leaks. The company has also established dedicated customer support channels to address user inquiries and reports of potential secondary damage. In case of confirmed incidents, the company will promptly notify affected users and take necessary actions.
LINE Yahoo reiterates its commitment to preventing future incidents by implementing the outlined measures, enhancing transparency, and collaborating with relevant authorities. They aim to regain user trust and ensure the secure and reliable operation of their services.
Please follow us to read more about Finance & FinTech in Japan, like hundreds of readers do every day. We invite you to also register for our short weekly digest, the “Japan FinTech Observer”, on Medium or on LinkedIn.
We also provide a daily short-form Japan FinTech Observer news podcast, available via its Podcast Page. Our global Finance & FinTech Podcast, “eXponential Finance” is available through its own LinkedIn newsletter, or via its Podcast Page.
Should you live in Tokyo, or just pass through, please also join our meetup. In any case, our YouTube channel and LinkedIn page are there for you as well.