Mission to Tallinn: Cybernetica

The sixth, and penultimate corporate stop of our "ICT & FinTech Mission to Tallinn" last week, courtesy of Enterprise Estonia, led us to Cybernetica, where we were hosted by Sales & Business Development Representative Maarja Suiste from the Data Exchange Department, who talked us through Cybernetica’s role as a foundational architect of the e-Estonia ecosystem and its expansion as a global technology provider. Suiste covered the company’s historical roots in academia, its transformation into a private R&D powerhouse, and its two primary export technologies: Data Exchange (interoperability via UXP) and Digital Identity (authentication/signing via SplitKey).
Key takeaways include Cybernetica’s unique position as a research-driven commercial entity, its deployment of mission-critical systems in over 35 countries—including significant projects in Ukraine, Benin, and Japan—and its strategic focus on post-quantum cryptography and privacy-enhancing technologies. The meeting also addressed specific questions regarding decentralized architecture, data privacy in the financial sector, and the resilience of digital governance during geopolitical crises.
1. Company Profile & Heritage
1.1. Roots in Academia and R&D
Cybernetica distinguishes itself from standard IT providers through its deep roots in scientific research. The organization originated in the 1960s as the Institute of Cybernetics, a purely academic institution. It transitioned into a private company, Cybernetica AS, in 1997.
Despite its privatization, the company maintains a heavy emphasis on Research and Development (R&D). Cybernetica currently employs a significant number of scientists who have published over 460 accredited research articles since 1992.
This academic rigor allows the company to collaborate with high-level defense and security organizations, including DARPA (the research arm of the US Department of Defense), NATO, and the European Space Agency (ESA).
1.2. Architects of e-Estonia
Cybernetica is widely recognized as a primary architect of the "e-Estonia" ecosystem. The company was instrumental in developing the critical layers that allowed the Estonian government to digitize 100% of its services. Key contributions include:
- X-Road: The backbone of Estonian interoperability.
- i-Voting: The internet voting system used in national elections.
- e-Customs: Digital customs and tax solutions.
- Smart-ID: A digital identity solution powered by their proprietary SplitKey technology.
Suiste noted that Estonia’s digital success relies on the "Once-Only Principle," where data is stored in distributed systems but accessed seamlessly across agencies, preventing data duplication and bureaucracy.
2. Core Domain #1: Interoperability & Data Exchange
2.1. The Challenge of Siloed Data
Suiste highlighted the traditional administrative burden faced by citizens in non-digitized societies. In the "old" model, citizens act as couriers, physically carrying paper documents from one agency (e.g., a tax board) to another (e.g., a bank) because these organizations operate in "silos" and cannot communicate directly. This results in inefficiency, data duplication, and frustration.
2.2. Unified eXchange Platform (UXP)
Cybernetica’s flagship interoperability product is UXP (Unified eXchange Platform). It acts as the "seamless backbone of a digital society," enabling secure, encrypted data exchange between disparate organizations without requiring a central database.
Key Architectural Principles:
- Decentralization: There is no "super-database" or central point of failure. Data remains with the original owner (the agency), and UXP facilitates the secure pipe between them.
- Standardized Governance: It allows a governing authority to manage an ecosystem of thousands of entities using a unified framework.
- Scalability: The system supports billions of transactions and thousands of services.
2.3. Case Study: The Estonian Tax Declaration
To illustrate the power of interoperability, Suiste detailed the Estonian income tax declaration process.
- Traditional Process: Takes 15–21 days. Requires gathering slips from employers, banks, and charities, filling out forms, and submitting them manually.
- The Digital Process: Takes approximately 3 minutes.
- The citizen logs into the Tax Board portal via Digital Identity.
- The Tax Board’s system automatically queries the Bank API (for investment data), the Employer’s system (for income data), and the Population Registry (for family status).
- The form is pre-filled. The citizen simply reviews and clicks "Submit".
This example demonstrates a "whole-of-society" approach where public and private sector data (e.g., banks) are integrated into a government service.
3. Core Domain #2: Digital Identity
3.1. SplitKey Technology
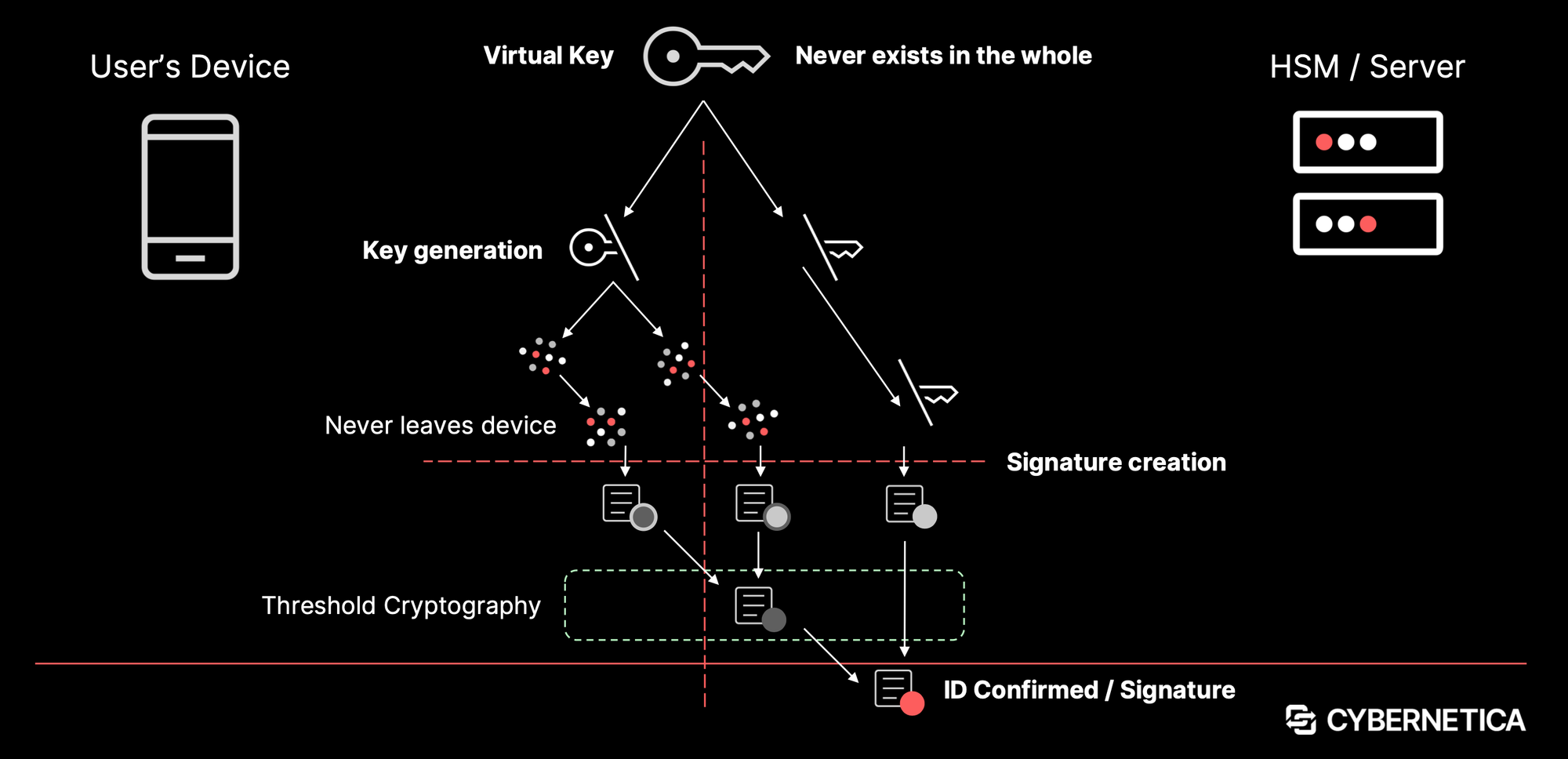
The second major pillar of Cybernetica’s portfolio is Digital Identity, powered by their patented technology, SplitKey. This technology turns a user's smartphone into a secure authentication and signing device.
How it Works:
- Threshold Cryptography: The user's private key is never stored in one place. It is cryptographically split into shares.
- Share Distribution: One share is stored on the user’s mobile device (app), and the other share is stored on a server/HSM (Hardware Security Module).
- Execution: When a user authenticates or signs a document, the two shares cooperate to perform the cryptographic operation without ever merging into a complete key on any single device. This makes the key mathematically un-copyable and highly secure against theft.
3.2. Smart-ID Use Case
SplitKey powers the Smart-ID service, which is the dominant digital identity solution in the Baltic states (Estonia, Latvia, Lithuania) and Iceland.
- Adoption: 3 million monthly active users conducting 75 million transactions per month.
- Ecosystem: It is used by top Nordic banks, telecommunications companies, and government portals. It enables legally binding digital signatures equivalent to handwritten signatures.
3.3. Future-Proofing: The EU Digital Wallet
Cybernetica is actively involved in the development of the European Digital Identity (EUDI) Wallet. This initiative aims to create a cross-border digital wallet for all EU citizens to store not just identity data, but also drivers' licenses, university diplomas, and prescriptions. Cybernetica is advising the Estonian Information System Authority on the architecture of this wallet to ensure compatibility with existing infrastructure.
4. Global Operations & Strategic Projects
Cybernetica has exported its technologies to over 40 countries. Suiste highlighted several high-impact implementations:
4.1. Ukraine: Resilience Through Digital Infrastructure
Since 2017, Cybernetica has partnered with Ukraine to implement Trembita, the national data exchange platform based on UXP.
- Scale: It powers the "Diia" app, delivering ~400 government services to 44 million people.
- Resilience: Despite the ongoing war and cyberattacks, the decentralized nature of Trembita has allowed the Ukrainian state to continue functioning digitally. It has handled approximately 14 billion transactions.
4.2. Benin: Leapfrogging to Digital Governance
In Benin (West Africa), Cybernetica implemented a full-scale interoperability platform and government portal starting in 2019.
- Result: Benin quickly became a regional benchmark for e-government, deploying over 400 online services and connecting nearly 70 organizations. This proves that developing nations can "leapfrog" legacy bureaucracy by adopting modular digital building blocks.
4.3. Malaysia: Scaling Up
Cybernetica is upgrading Malaysia’s existing government data exchange (MyGDX) to UXP. The goal is to support a 6x growth in digital government usage for a population of 33 million.
4.4. Japan: Strategic Partnerships
Cybernetica has a significant and growing presence in Japan through partnerships with major corporations.
- Sumitomo Mitsui Trust Bank (SMTB): Conducting Proofs of Concept (PoC) focusing on "information banking" and healthcare data exchange.
- NTT Data: Collaborating on a cross-border health data exchange PoC between Japan and the EU. This involves Japanese citizens traveling to the EU and needing access to their medical records.
- Nichigas: Utilizing UXP for internal data exchange across multiple departments and group companies to streamline operations.
- NTT Security: Developing cybersecurity awareness systems based on Cybernetica's visualization technologies.
5. Other Specialized Departments
While Data Exchange and Digital Identity were the primary focus, Cybernetica also provides capabilities in other critical sectors:
5.1. Maritime & Border Surveillance
Cybernetica maintains a unit dedicated to Vessel Traffic Management Systems (VTMS) and radio communication. They act as a system integrator for radars, sensors, and radios to provide a unified picture of maritime traffic.
- Key Projects: They monitor traffic in the Strait of Gibraltar (reporting to Morocco) and the Malacca Strait (for Malaysia and Indonesia), two of the busiest waterways in the world.
5.2. Cybersecurity Services
The company offers proactive cybersecurity services, including penetration testing, vulnerability assessments, and core security consulting.
- Red Teaming: They perform "friendly attacks" to test organizational defenses.
- NATO Cooperation: Cybernetica participates in "Locked Shields," the world’s largest live-fire cyber defense exercise organized by the NATO Cooperative Cyber Defence Centre of Excellence in Estonia.
5.3. Privacy Technologies
Cybernetica develops Sharemind, a privacy-preserving technology that allows parties to analyze sensitive data (e.g., tax or health records) without actually seeing the individual values. This is used for statistical analysis and policy making where privacy laws (like GDPR) are strict.
6. Meeting Q&A and Technical Discussion
During the session, several key technical and operational questions were raised by the attendees.
Q: How does the decentralized data exchange (UXP) actually work if there is no central server? How do agencies find each other?
- Answer: While the data is decentralized (moving peer-to-peer between agencies), the governance is centralized. There is a central "address book" or registry. When Agency A needs data from Agency B, it looks up Agency B's secure address and technical capabilities in this central registry. However, the data payload travels directly from A to B, encrypted, without passing through the central server. This ensures the central authority cannot spy on the data or become a bottleneck.
Q: In the financial sector, specifically regarding the "Consent" mentioned in the tax example, how is that managed?
- Answer: In the Estonian model, when a user logs into a bank or tax portal, their digital identity (SplitKey/Smart-ID) authenticates them. For specific data sharing (e.g., sending investment info to the tax board), the user provides consent via the digital channel. In some cases, like tax declarations, the legal framework mandates the data availability, but the user initiates the query by starting the declaration. The system ensures that banks do not need to send physical papers; they simply expose an API that the Tax Board can query upon the user's request.
Q: Regarding the "SplitKey" technology, does it require the user to have a specific hardware token or SIM card?
- Answer: No. SplitKey is software-based. It is an "Over-the-Top" (OTT) solution, meaning it works as a standard mobile app on iOS or Android. It does not require a special SIM card (unlike Mobile-ID) or a card reader (unlike the ID-card). This lowers the barrier to entry and cost for deployment.
Q: How does Cybernetica handle cybersecurity for its own clients?
- Answer: Cybernetica builds security into the architecture (security-by-design). Additionally, they offer "Managed Detection and Response" (though the specific product name "MDR" was debated, the concept was confirmed). They monitor systems for anomalies. Suiste alluded to a new intrusion detection product launching soon that uses AI to detect anomalies in network traffic.
Q: Is Cybernetica involved in offensive cyber operations?
- Answer: The company focuses on defensive technologies and resilience. However, through their cybersecurity services division, they conduct authorized "Red Teaming" exercises where they simulate attacks to help clients (including governments and critical infrastructure providers) strengthen their defenses.
7. Future Outlook
The presentation concluded with a look at emerging technologies:
- Post-Quantum Cryptography (PQC): Cybernetica is actively researching cryptographic transitions. As quantum computers threaten current encryption standards, Cybernetica is preparing its SplitKey and UXP solutions to be "quantum-safe" to ensure long-term data protection.
- AI & Machine Learning: The company is integrating AI into its surveillance and cybersecurity products to automate threat detection and situational awareness.
- e-Democracy: Continuing to refine Internet Voting technologies to ensure they remain secure and transparent for future elections.
8. Conclusion
Cybernetica presented itself not merely as a software vendor, but as a strategic partner for nation-scale digital transformation. Their experience in building e-Estonia, combined with a scientific approach to R&D, allows them to offer solutions that are secure, scalable, and proven in some of the most challenging environments globally (e.g., Ukraine).
For the Japanese market, Cybernetica offers a compelling value proposition: a decentralized, privacy-centric approach to data exchange and a high-security, user-friendly mobile identity solution—both of which address current challenges in Japan’s digital transformation journey.






